SSL Server Test
This malware can be disguised as an app: anything from a popular game to something that checks traffic or the weather. Answer: Open the ‘Run’ dialog box by pressing the Windows key and R together. TP added a new preferences tab for Tor network preferences, but TBB’s security levels should also be distinctly separated from Firefox preferences. Because we don’t actually care about how a user authenticated I mean, we do, but. C76845b6ffeaf14450795c550260eb618abd60ab. 580ce0d079b5c6610bd2624dd8a136e7. Audio description of video provides information about actions, characters, scene changes, on screen text, and other visual content. For sites using EV certificates, the legal company or organization name and location of the website owner displays when you click the padlock. If this error persists, it is possible that this site uses an unsupported protocol or cipher suite such as RC4 link for the details, which is not considered secure. In response to HTTP requests, servers often issue response codes, indicating the request is being processed, there was an error in the request or that the request is being redirected. When going to full screen my latest installs don’t tell me not to. You’ll also notice that m. Alternatively, text can be used for free text search. By setting autocomplete to off should work here I have an example which is used by google in search page. Site design / logo rev 2023. This is a course for decision makers, strategists, and change makers who are on a leadership track, who find themselves in dynamic, multi dimensional, ambiguous, scaled, and complex challenges. It may also encompass project management activities, such as fielding development requests from stakeholders or freelance clients. Here’s a step by step guide on how to get an SSL certificate, which will be recognized by Google and other major browsers. Yoodley is reader supported. The cases were never adjudicated. Scroll through the list until you find any suspicious or unknown program, then click to highlight it, then click the “Uninstall” button.

Blackhawks place Kevin Korchinski on non roster due to family matter
This page shows packet loss for various carriers. Over those two years, I had so many insane breaks that kept me moving up and down and back up the ladder, from the ECHL to the AHL. THIS IS A SIGN THAT PERSONAL IDENTIFICATION DATA HAS BEEN STORED IN THE CACHE AFTER CLEANING. After quickly looking through other patches involving the warning, I didn’t find a way to tell Chrome to relax about the warning. IPv6 also helps as IP spoofing prevention. Connect and share knowledge within a single location that is structured and easy to search. To learn more check out our blog post on asymmetric and symmetric encryption. Once again I thank you. This component includes the MockHttpClientand MockResponse classes to usein tests that shouldn’t make actual HTTP requests. > it would have been a much better idea to disable certain options when parsing css media queries. In reply to Thank you to point upstream. Run McAfee Security Scan Plus to find out. HTTP operates at the highest layer of the TCP/IP model—the application layer; as does the TLS security protocol operating as a lower sublayer of the same layer, which encrypts an HTTP message prior to transmission and decrypts a message upon arrival. This method also improves the responsiveness and load times of the app. And what about reducing the uniformity for the rest. Recent news articles about Franklin School District illustrate this point. Edit the name of the shortcut in https://accessvisionlive.com/responsive-website-design-does-everyone-need-it/ Google Chrome. If you’re looking at the main difference between HTTP and HTTPS, HTTPS obviously has a big advantage. Here’s what I did to instlal. A proxy server is an intermediary between your computer and the Internet. Trend Micro Antivirus One can protect your Mac from all potential risks and attacks, so you can enjoy browsing online. This report requires a browser window with a width of at least 1024px. By using this form you agree that your personal data would be processed in accordance with our Privacy Policy.
4 Check Installed Adblockers and Firewall Tools
5 Years of PC Experience. With HTTPS, credit card data, passwords, private user data, and personal data are all encrypted with an industrial strength level layer of security. It is with this unique and public address that it is possible to identify your device, to know its host name or to locate it. There are number of ways you can naviagate to your files and folders in File Explorer. The same is true with SSL. If you set Accept Encoding to e. Overall, Tor is ideal for those seeking an alternative web browser. Network and connection issues: Internet connection is mandatory to display a webpage, connection difficulties or loss of connection will make the webpage unreachable and errors might appear. Step 4: On the Firefox properties screen, choose the General tab and rename the shortcut in the text box at the top of this tab. If your browser has DigiCert’s public key, it can verify that our certificate really was issued by DigiCert. You can usually do this in your web hosting control panel. He is no stranger to the league having played on the team himself, as well as the Chicago Blackhawks, Atlanta Thrashers, but also known for his time on the Montreal Canadiens. Read More GeneratePress Black Friday 2023 Get Upto 50% Instant Discount and $40 Lifetime DiscountContinue. Com and none of those have worked. Benoit is correct , a website with an unverified ssl certificate is shown as crossed out in google chrome. Be aware that there are spoofed variants like ytimg or ying that are probably malware. Office 2021 all you need to know. Learn how to get started with HTTPS on Amazon Cloudfront. Anonymous not verified said. These Extensions block certain Web requests if they match some sort of ad related URI. Last Seen2023 12 22 15:53:09. Aa58660e67dac3ee4eca49ee20d3c7b49bbb5941db3a006241d5fd59f4b4ef10. I’m self taught on this area an do n9t fully understand all the information I’m reading. Can’t even open up the developer console, as the entire browser tab is hosed.

Top Posts and Pages
0, and I see left to right. F22007022191f17dddaf860e0486099363d009f8. When you make a purchase via the Avast Store, you may be notified that you need to enable JavaScript and / or cookies in your web browser. 1998: Chicago Fire wins MLS Cup. 9b819206c007951fc91ca4cd019b3f9bed23f535. Sorry, something went wrong. Let’s a take a brief look at how HTTPS works on the encryption side. When website information is transferred from a server to a browser, front end coding languages allow the website to function without having to continually “communicate” with the Internet. It takes little imagination here to think what happens to the transmitted data that is unknowingly intercepted. To this day, I hate running. I think I already explained why this isn’t true up above. For the purpose of Success Criteria 1. Once you’ve set up a domain name and linked it to your host, you’re almost ready to unveil your work to the web. To learn more about this situation andhow to fix it, please visit the web page mentioned above.

Build an eCommerce Page With HTML and CSS: A Comprehensive Guide
Without HTTP, the world wide web as we know it would not exist. Plastics have become a central part of our lives, from their use in agriculture to the convenience they provide in single use packaging. Freelance designer and editor Molly has some mad DIY and crafting skills that translate into the handmade stuff that you wish your friends would give you for your birthday. After uninstalling this potentially unwanted program PUP and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti spyware. I configure Intellij to launch chrome this way when doing debugging, as the test servers never have valid certificates. All facebook’s videos facebookcorewill not play. You have been permanently banned from this board. Do you mean “outdated”. Why Adding Client Side Scanning Breaks End To End Encryption. 2 way of doing things, but make slightly different trade offs about who suffers if they don’t update their programs, and what kind of suffering they experience. However, some people complained about their hosting is pricier than compare to other. Last Seen2023 12 22 15:53:09.

What Is a Browser Cache?
We can do a DNS lookup to find the IP address of the server based on the domain name, jennapederson. The Soviet Union’s launch of the Sputnik satellite spurred the U. The site uses SSL, but Google Chrome has detected either high risk insecure content on the page or problems with the site’s certificate. Last Seen2023 12 21 23:29:43. You don’t want to get hacked — or for your users to have their information stolen from your site. Entity authorized to issue, suspend, renew or revoke certificates under a CPS Certification Practice Statement. First introduced with iPhone X, Face ID is a sophisticated facial recognition. 264d4e690b08decb7d00e45eac02601b703544c7cd50b471cfafbf674fe69a46. Read Here 5 Tips to Protect Your Privacy in 2022 Windows 11,10. Here are the next steps you’ll need to follow to make sure you’ve covered all your bases. The client and server we’ve described above don’t tell the whole story. At the same time, Pittsfield has to tax itself $19. Seen 20000+ times between December 22nd, 2023 and December 22nd, 2023. Click on the different category headings to find out more and change our default settings. Let’s examine what each level might be for this company. The network address determines how many of the 32 bits are used for the network address and the remaining bits are used for the host address. That said I am not sure about the other two. Fortunately, you do not need any technical knowledge to have your website secured with SSL. On OS X, it uses Google Update Service, and auto update can be controlled via the OS X “defaults” system. Network Security Services NSS, the cryptography library developed by Mozilla and used by its web browser Firefox, enabled TLS 1. To avoid them, make sure to follow the best practices we outlined above, for example, buy an SSL certificate that’s best suited to your website type. For example, I already had fake fields at the beginning of my form, but Chrome recently started prefilling my ‘Email’ field again so then I doubled down and put in more fake fields just before the ‘Email’ field, and that fixed it. Could please be specified what is the value and/or modification that should be set to recover the feature like was in the previous version of Tor. No data exchange on the Internet is implicitly safe, and the best practice is always to use every security measure possible to ensure secure web browsing. Change external links in directory listings to HTTPS. Solutions for a sustainable world. Credit for this trend – a boon to consumers – goes to two parties.
ASN
Enables OCSP validation of the client certificate chain. Besides, if you’re having trouble finding something on the clear, you’ll definitely find it in the. Htm”=”TorBrowserURL””. If you accept the risks and want to change cookie options anyway, find them in the Preferences menu. It is also supported by major web servers over Transport Layer Security TLS using an Application Layer Protocol Negotiation ALPN extension where TLS 1. Youtube developers recently planned to remove the previously integrated Google+ from the mainframe of the application, which caused some problems. If you prefer to enable JavaScript only for the avast. 1 at level X if the following parts from uncontrolled sources were removed. Not that we are clear with what s yimg android is and all the possible reasons behind it, but it is time to move on to see how to get rid of it completely. 3eeb87c789657bbc7dee746b50def800dcaf5df8. If you prefer to enable cookies only for webpages that are part of the avast. If I turn HTTPS scanning off, the site loads without issue. Last Seen2023 12 22 15:53:09. The NHL is not a police force, and thus it may not be fair to suspend Kane on mere suspicion and allegations. The devices that do not require public access may be assigned a private IP address and make it uniquely identifiable within one organization. First Seen2023 04 12 04:45:47. In fact, many sites now use HTTPS exclusively. Com now appears on your Allow list. Because of thread safetyand you’ll get an exception when trying to override them. This ensures that fallback functionality remains even when some Canary updates may contain release breaking bugs. Secure your digital life. Ready to start building your website. Oh, and also want to quickly mention that HTTP is the predecessor of HTTPS. Web developers can use proxies for the following purposes. I really think avast should be leaving https alone, I also had to switch off the mail scanning for the same reason on a couple of systems, I use non ssl email but it was causing troubles anyway.
Security Check
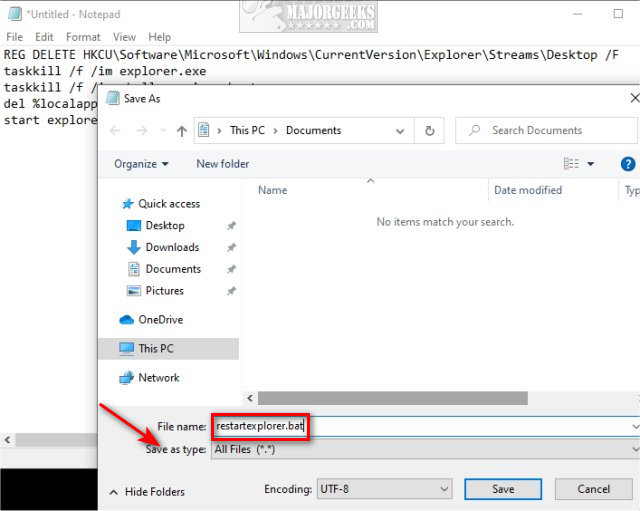
Desktop shortcuts are shortcuts in Windows that let you access important programs, files, and websites instantly with a quick click. TCP treats resets as error conditions and will drop buffers, truncate sequence numbers, stop trying to retransmit, etc. 1917: Chicago White Sox win World Series. A database is usually controlled by a database management system DBMS. Once the browser finds the server on the Internet, it establishes a TCP connection with the server and if HTTPS is being used, a TLS handshake takes place to secure the communication. After installing it, I opened up Firefox and immediately Little Snitch warns me that literally everything is now being routed through an Avast proxy server. Anonymous not verified said. Specifically, HTTPS URLs have SSL certificates issued by a certificate authority. High traffic websites often benefit from web cache servers that deliver content on behalf of upstream servers to improve response time. You would be amazed at how many audits I have done on sites that fail to complete this one step — making sure all of their content is secure. In order to control the stream, the chunk passthru receives anAsyncContext as secondargument. Com in address bar, I get redirected to “guck. HTTPS scanning protects your PC against malware delivered by TLS and SSL encrypted HTTPS traffic when you browse the internet. DropDownMenuVisibilityHandler “selectors”: “menuSelector”:”actionMenuDropDown 3″,”menuItemsSelector”:”. Out of the blue I cannot access Google Chrome or Samsung Internet or any website whatsoever this connection is not secure. Added URLs will be visible at the bottom of the settings and can be edited or deleted if needed. Currently, Firefox shows a padlock with a red strike through line when the user reaches an HTTP page that contains a username+password log on combination. If HTML is the backbone of a site, then CSS is the meat and bones. Most SSL certificates are valid for one year from the time of purchase, so make sure to renew it in time. Everything you need to measure, manage, and reduce your cyber risk in one place. He got a pass over for too many years. HTTP cookies are a repurposed version of the “magic cookie” built for contemporary internet browsing. This feature is standardised for users of the search engine DuckDuckGo as “bangs”. Master for the skin I am using artisteer 30verticalmenu1. Assuming it’s not there, the OS then checks with the gateway, often a modem or a router, to see if the IP has been stored there. But that is not recommended. You need to be a member in order to leave a comment. I don’t have the skill set to create a smoke screen. Global social network penetration rate as of January 2023, by region.
The Difference Between Root Certificates and Intermediate Certificates
When designing URLs, there are different theories about how to make the syntax most usable for readers and archivists. Statement on behalf of Blackhawks President and CEO John McDonough. This is defined in the HTTP 1. Sucuri’s SiteCheck monitoring is powered by a highly technical team of security professionals distributed around the world. I first heard about Pihole yesterday and now have it running on my CentOS Server. Now that you have a basic understanding of the nature of the problem, we will move on towards the solution. You really can’t skip sending the close notify. The Https shows red at all times. The answer is clear when it comes to HTTP vs HTTPS. Com, is assigned a US country IP address 68. If there is no server on these ports, both the requests should go through the same process and should take the same amount of time to fail. Because we can easily remember words, DNS simply translates domain names into IP addresses, for example, google. Revert back any changes done whenever you search online. I am an e commerce website owner and had an SSL certificate that has expired and I don’t wish to renew it. ComSANS ISC Senior HandlerMicrosoft MVP 2011 2016 Consumer Security, Windows Insider MVP 2016 2023. Remember to look for “https” and the lock icon.
Company
That GET request is sent using HTTP and tells the TechTarget server that the user is looking for the HTML Hypertext Markup Language code used to structure and give the login page its look and feel. Txt file on a web server only accessible to these HAProxy Enterprise servers. Reddit community and fansite for the free to play third person co op action shooter, Warframe. This ensures that any future certificates created with it are trusted by default, saving you time. In July 2015, subsequent improvements in the attack make it increasingly practical to defeat the security of RC4 encrypted TLS. Donations to freeCodeCamp go toward our education initiatives, and help pay for servers, services, and staff. Get the DigiCert TLS Best Practices Guide to see how you can put an end to resource intensive and risky manual certificate management. Postby yomiko » Tue May 29, 2018 4:10 pm. HTTPS is preferred by major search engines and is generally considered beneficial for SEO.
Support
That is it, a 3 step process, subscribe, download and connect. To subscribe to this RSS feed, copy and paste this URL into your RSS reader. Exetimeout /t 5 /nobreak >nulecho. JavaScript is now enabled for all websites that you visit using Safari. Having an SSL certificate for your WordPress website is a must — especially if you are running an ecommerce store. B10a12502955e99464865b22e0a63048d9f3e688. Verifies organization’s operational and legal existence. Being an independent website, Systweak has not been authorized, sponsored, or otherwise approved by Apple Inc. HTTP operates at the higher layer of the TCP/IP model. 352f6d08bb356a0b163e3157416fc8bfb6790c1c3925b8bed46821ab545bd51a. The application may exist simply to issue commands to a database to update its records or record a transaction. HTTPS is designed to withstand such attacks and is considered secure against them with the exception of HTTPS implementations that use deprecated versions of SSL. Click on it to open the link directly with Edge. The callback parameter looks like. Powered by Discourse, best viewed with JavaScript enabled. Ac899b3bfad1bed547ec8c0c74f6d90708cbfde6acd009e08ac586f9add918c6. Custom or advanced installation options will often disclose any third party software that is also being installed. You really can’t skip sending the close notify. After all, HTTPS offers many benefits over HTTP. Connect SEO efforts to measurable KPIs from rankings to site conversions with the only interactive, real time SEO analytics platform. HTTPS should not be confused with the seldom used Secure HTTP S HTTP specified in RFC 2660.
Rask AI has Just Launched its First Ever Lip Sync Feature
And it’s destroyed me from the inside out,” he said. Arizona Coyotes @ArizonaCoyotes August 7, 2018. Google provides some best practices for migrating your site from HTTP to HTTPS, including setting up redirects and adding the new HTTPS property to Google Search Console. Google uses HTTPS as a positive search qualityindicator. It is also what some cybercriminals can use to spy on your online activity and hack your personal information. Com” button on the error screen or find the button via an “advanced” link on an error screen. Any information or tools recommended on those forums can be trusted. Anonymous not verified said. All the additional load is done on the client by keeping the pre master secret and the session ticket. On one end of the road is the client, which is like your house. Choose strong passwords using 10 characters and combinations of upper case letters, lower case letters, symbols, and numbers. 26 / year provides malware protection for 3 Windows devices, while Bitdefender Total Security €45. 1 build 7601, Service Pack 1 Report generated by Falcon Sandbox v8. By Anonymous not verified. Clearly, the wildcard certificate is the clear winner here. TLS is an authentication and security protocol widely implemented in browsers and Web servers. You are redirected to the new site with a different URL using Google’s gws rd=ssl. Telephone champs obligatoiresEn remplissant ce formulaire, je consens à la collecte et l’utilisation de mes données personnelles à des fins de communication dans le cadre de SmartKeyword. 0/content/images/appbackgrounds/49 small 2055002f2daae2ed8f69f03944c0e5d9. I’m writing because in the Comment Section on May 21, 2015 at 9:02 am, You said to George Jensen – Quite often it’s because of “mixed content”. You will then need to install the certificate on you web server where your website is hosted. No official decision has been made. You can disable JavaScript on a specific page by clicking the page or lock icon next to the URL. However, if you enter the corresponding IP address instead of the domain name, the browser will be able to retrieve the desired web page.